SurfingAttack is probably one of the most innovative ways to carry out cyber-attacks by taking control of smart devices and place commands on them using sonic waves.
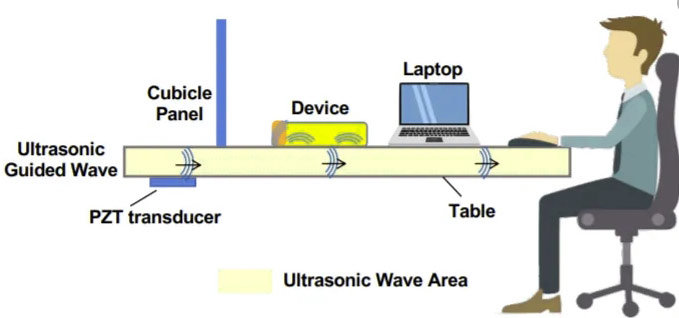
The hacking technique can use voice commands encoded in sonic waves to activate smart devices using a lot of stealth. The method enables mobile devices and allows the attacker to make phone calls or read your texts by proxy. SurfingAttack was introduced at the Network and Distributed Systems Security Symposium that took place in California just a few weeks ago.
It has been designed to enable interaction between a voice-controlled device and a third party other than the user. This is done over a long reach of distance and without using a line of sight. All the findings of this form of Continue reading “SurfingAttack – The Best Way to Hack Smartphones Using Ultrasonic Waves”





